You can see publications related to our project.
Realize the IC design protection andthe IC authenticity verification throughthe Security-by-Design approach
Realize the IC designprotection and the IC authenticity verification throughthe Security-by-Design approach
TRustworthy Architecture, Cryptography, and Evaluation for IoT systems

PROJECT
What the project aims for
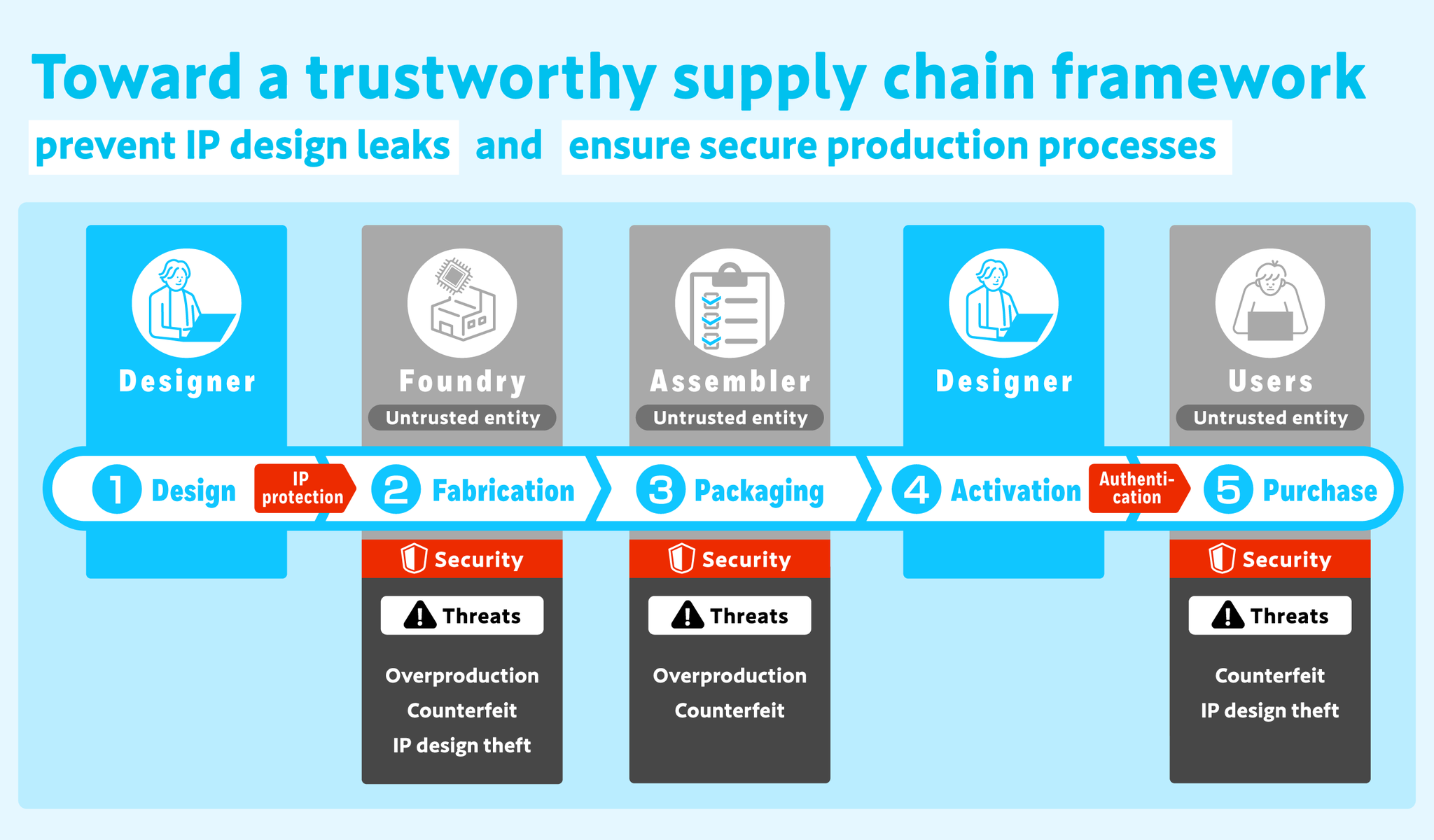
Development ofDesign Fundamentalsfor Trustworthy IoT Systems
Semiconductors (ICs) play an important role in supporting the information society, such as communication technology and energy supply. When an outside company is involved in the manufacturing of ICs, the threat of IC design technology leakage and unauthorized products (unauthorized manufacturing, counterfeit products, etc.) is unavoidable. In addition, since the distribution of unauthorized products can lead to problems that cause damage to users, it is vital to have a system that can confirm that the products have passed through the authorized IC manufacturing route.
In this project, we will extract and formalize the security requirements of the entire IC supply chain, which is the infrastructure for Society 5.0, and develop a new IoT system design scheme that collectively realizes the protection of IC design technology and the verification of IC authenticity, i.e., verifying whether the product has passed through the legitimate manufacturing route, by the user. We will realize this scheme satisfying the above security requirements based on the theory of advanced cryptography. We aim to develop a system design method and its design environment to realize this scheme in the security-by-design framework and quantify the trade-off between security levels depending on the use cases of IoT systems and implementation costs.
GROUP
Research Groups
-
 See details
See detailsResearch Groups
The Archtecture Group develops and integrates design technology (hardware/software co-design) to implement the established IP protection and device authenticity verification technologies with Security-by-Design principles. The group incorporates this into real-world systems and focuses on advancing the design environment.
-
 See details
See detailsAdvanced
Cryptography GroupThe Advanced Cryptography Group focuses on formalizing and designing provably secure IP protection and device authenticity verification technologies for a trustworthy IC supply chain and IoT system design infrastructure.
-
 See details
See detailsEvaluation and
Modeling GroupThe Evaluation and Modeling Group focuses on implementation-aware modeling for the developed IP protection and device authenticity verification technologies. The group also develops security metrics and a simulation environment for the quantitative evaluation of these technologies within a trustworthy IC supply chain and IoT system design infrastructure.